What Is Third-Party Risk Management (TPRM)?
Third-Party Risk Management (TPRM) is the process of identifying, assessing, and mitigating risks associated with outsourcing to external vendors, suppliers, or service providers. These risks span financial, reputational, operational, and cybersecurity domains.
Vendors often handle sensitive information like intellectual property, personally identifiable information (PII), or protected health information (PHI), making TPRM an essential aspect of cybersecurity programs to safeguard business operations.
What Is a Third Party?
A third party refers to any external entity your organization collaborates with, including:
- Suppliers
- Manufacturers
- Service providers
- Distributors and resellers
- Agents and affiliates
They can operate upstream (suppliers) or downstream (distributors) within your value chain. Third parties might provide critical services such as SaaS tools, supply chain logistics, or financial support, emphasizing their integral role in daily operations.
Difference Between Third-Party and Fourth-Party Risks
While third parties are entities your organization directly engages with, fourth parties are the vendors of your vendors. These relationships introduce additional risks as they extend beyond your immediate contractual obligations. Understanding and mitigating fourth-party risks is vital to securing your entire supply chain.
Why Is Third-Party Risk Management Important?
Third-party relationships amplify your organization’s cybersecurity complexity due to:
- Increased attack surface: Vendors may introduce vulnerabilities hackers can exploit.
- Lack of transparency: You have limited visibility into their security practices.
- Regulatory implications: Laws like GDPR and CCPA hold organizations accountable for vendor-related data breaches.
- Real-world incidents: Examples like the Target data breach, caused by a vendor’s weak security, highlight the high stakes.
Common Risks Introduced by Third Parties
- Cybersecurity Risk: Exposure to cyberattacks and data breaches.
- Operational Risk: Disruptions to business continuity due to vendor failures.
- Compliance Risk: Non-compliance with industry regulations or standards.
- Reputational Risk: Damage from poor vendor practices or data breaches.
- Financial Risk: Economic losses caused by vendor shortcomings.
- Strategic Risk: Hindered business objectives due to vendor dependencies.
Benefits of Investing in Third-Party Risk Management
- Cost Reduction: Prevent expensive breaches (average cost: $4.55 million).
- Regulatory Compliance: Meet requirements like GDPR, FISMA, and NIST standards.
- Risk Mitigation: Minimize data security and operational risks.
- Improved Decision-Making: Gain visibility and control over your vendor network.
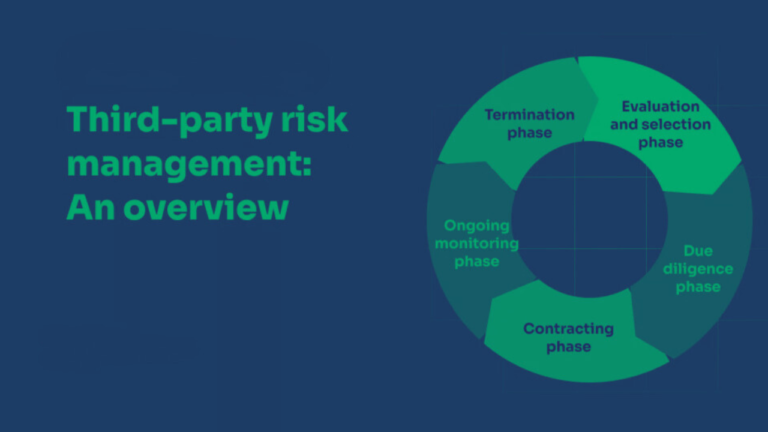
Steps to Implement TPRM in Your Organization
- Develop a Risk Assessment Framework: Identify and evaluate risks for each vendor.
- Perform Due Diligence: Screen vendors thoroughly before onboarding.
- Establish Contracts: Define SLAs, compliance expectations, and security requirements.
- Continuous Monitoring: Regularly assess vendor performance and risk levels.
- Implement Incident Response Plans: Prepare for potential third-party security incidents.
Implementing a Third-Party Risk Management Program
Steps to Develop a Third-Party Risk Management Framework
1. Analysis
Before onboarding a vendor, identify potential risks and the level of due diligence required. This includes assessing the vendor’s external security posture. Tools like security ratings can provide insight into their cybersecurity standards.
- Pro Tip: Compare third-party risk profiles against your organization’s defined risk appetite.
2. Engagement
Once a vendor meets your baseline security standards, gather deeper insights via security questionnaires. These questionnaires assess their internal controls and policies.
- Automation Tip: Use platforms like UpGuard Vendor Risk to streamline questionnaire workflows.
3. Remediation
Address unacceptable risks before onboarding. A robust remediation process ensures issues are tracked, prioritized, and resolved efficiently.
- Solution Highlight: Platforms with remediation workflows can simplify this process, ensuring critical risks are handled promptly.
4. Approval
Evaluate the vendor’s risk profile after remediation and decide on onboarding. Consider risk tolerance, vendor criticality, and compliance requirements during the decision-making process.
5. Continuous Monitoring
Monitoring does not stop at onboarding. Implement Continuous Security Monitoring (CSM) to track vendors’ cybersecurity postures and identify emerging threats.
Key Components of a Vendor Management Policy
A vendor management policy identifies high-risk vendors and defines controls to mitigate third-party and fourth-party risks. Elements include:
- Minimum security standards for contracts
- Annual inspections or audits
- Transition plans for underperforming vendors
- Compliance with SOC 2 or similar standards for critical vendors
Methods to Evaluate Third Parties
1. Security Ratings
These data-driven scores provide a real-time assessment of a vendor’s cybersecurity posture, offering insights into risks and vulnerabilities.
2. Security Questionnaires
Standardized questionnaires uncover weaknesses in vendors’ security measures.
3. Penetration Testing
Ethical hacking tests the resilience of a vendor’s systems against potential cyberattacks.
4. Virtual and Onsite Evaluations
Physical and procedural assessments of vendors’ compliance with security standards.
Common Challenges in TPRM
1. Lack of Speed
Lengthy assessment processes slow down vendor onboarding. Automated tools can significantly accelerate this.
2. Lack of Visibility
Traditional methods like point-in-time evaluations fail to capture dynamic risks. Continuous monitoring bridges this gap.
3. Lack of Consistency
Inconsistent risk assessments lead to overlooked vulnerabilities. Standardizing processes ensures comprehensive evaluations.
4. Lack of Engagement
Vendors may delay responses to security questionnaires. Centralized platforms with in-line correspondence can streamline communication.
5. Lack of Context
Understanding the criticality of each vendor is crucial. Label vendors by importance to prioritize high-risk relationships effectively.
Features to Look For in a TPRM Platform
1. Scalability and Automation
Ensure the platform supports managing numerous vendors with automated workflows.
2. Security Ratings and Questionnaires
Access to customizable, pre-built libraries for questionnaires and up-to-date security ratings.
3. Continuous Monitoring
Real-time tracking of vendors’ cybersecurity postures to mitigate risks proactively.
4. Reporting Capabilities
Comprehensive reports for stakeholders, boards, and regulators to demonstrate compliance and risk management efforts.
5. Fourth-Party Discovery
Understanding your vendors’ vendors (fourth parties) to ensure upstream and downstream security.
FAQs on Third-Party Risk Management
What is third-party risk management?
TPRM is a framework for identifying and mitigating risks originating from vendors and partners.
What is a third-party risk?
These are risks posed by external vendors, including cybersecurity, operational, legal, reputational, and financial threats.
How do you create a TPRM program?
- Identify vendors and assess their data access levels.
- Compare risks against organizational risk appetite.
- Implement controls to mitigate risks.
- Establish ongoing monitoring and compliance strategies.
By addressing these aspects, organizations can create resilient, scalable, and efficient TPRM programs to protect their operations and reputation.